Transactions Explained
The Interceptor provides a clear and detailed visualization of your what's actually happening in a transaction.
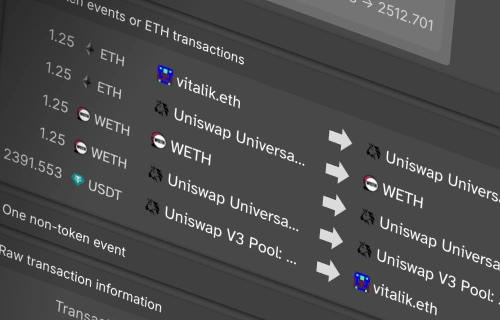
The Interceptor provides a clear and detailed visualization of your what's actually happening in a transaction.

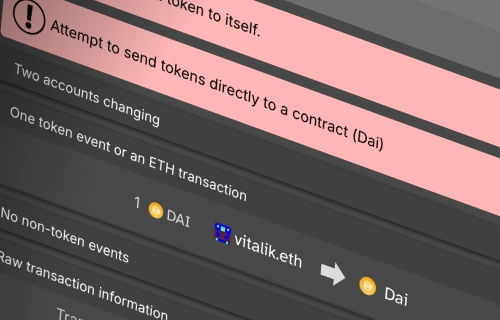
View the effects a transaction will have without executing it.
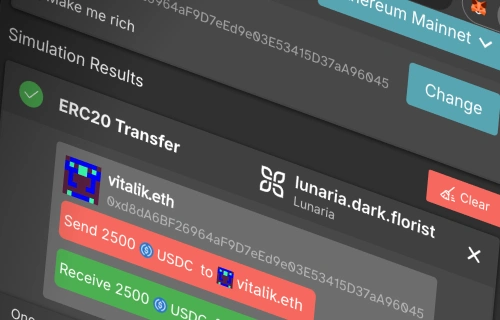
Don't let not having a private key prevent you from browsing as Vitalik.
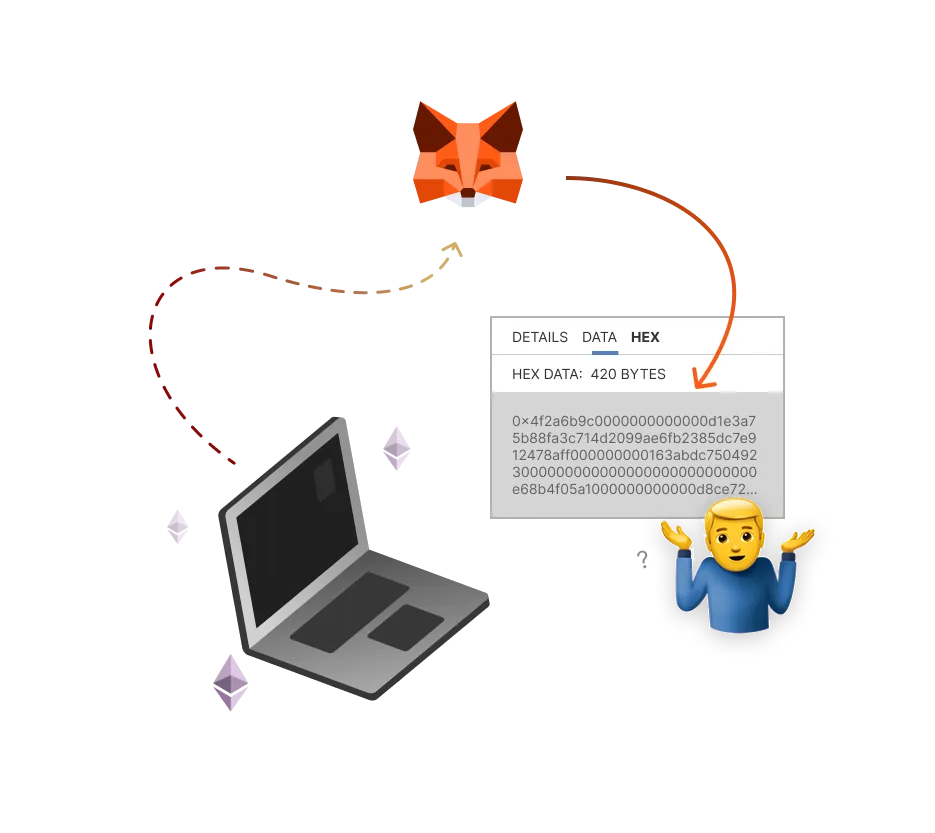
When you use a standard dApp, it connects directly to MetaMask, which generates transaction signatures that are often complex and hard to understand
Not understanding what you are signing can put you at significant risk, especially if you're not aware on how blockchain transactions work.
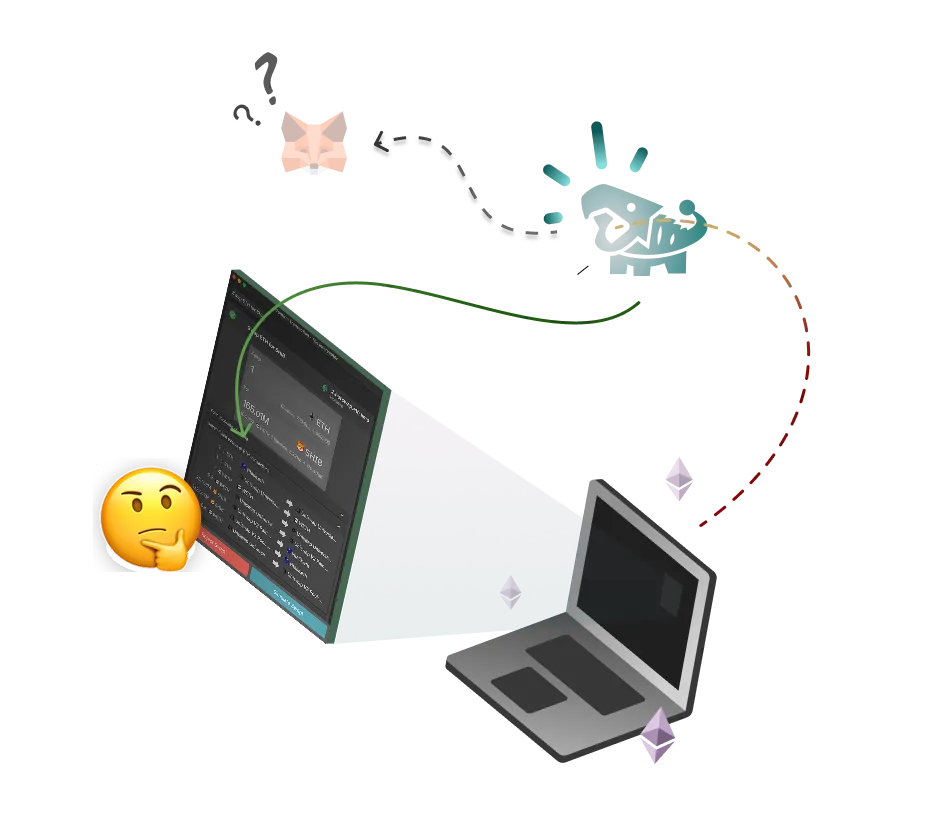
The Interceptor sits between the dApp and MetaMask, allowing it to 'intercept' transactions before they are signed. This enables Interceptor to provide clear simulation of a transaction, along with built-in protections.
Better insight into transactions allows you to make more informed decisions
A crypto scam is a malicious attempt to steal your crypto assets, consisting of two distinct parts: deceit—how a scammer tricks you, and payload—what the scammer does with your account.
Worried you might be getting scammed? Don't guess—join our Discord community for support and stay informed.
Join our Discord communitySimple mistakes can sometimes lead to significant financial losses. Here's a few of the common errors that would have been prevented by The Interceptor
Accidentally copying token addresses as recipient of tokens instean of intended destination
Token Approval is often used by scammers to steal your money later, while only usually required when interacting with a contract
Token Approval is often used by scammers to steal your money later, while only usually required when interacting with a contract
Token approvals to contracts not source verified on Etherscan
Setting gas price significantly above base fee.
Transferring funds to addresses flagged as scams or blacklisted destinations can result in permanent loss.
Dark Florist is an exceptional team of Ethereum developers who are tired of poor user experience and security of the current Ethereum wallet landscape and we are here to build things better.

Killari
Data Scientist

Micah Zoltu
Senior Blockchain Engineer

Jubal Mabaquiao
Software Engineer
Check out other products and tools we've designed to help you transact on the blockchain more smartly and securely

Token rescue dApp to send bundles to Flashbots.

Simple, decentralized token sender dApp

Simple, decentralized NFT sender dApp

A tool to create immutable ENS sub names

Open source and censorship resistant interface for the Uniswap protocol